Press Release: Universal Cloud Storage - Breaking Information and Features
Press Release: Universal Cloud Storage - Breaking Information and Features
Blog Article
Boost Effectiveness With Trustworthy Universal Cloud Provider
Embracing trustworthy global cloud services is vital in today's ever-evolving electronic landscape. The potential to enhance procedures, increase efficiency, and strengthen information safety and security with cloud remedies is a compelling proposal for services looking for enhanced performance. Nevertheless, the trip to using the full benefits of cloud services involves tactical decision-making and notified options. Discovering the subtleties of scalability, cooperation devices, and security steps can be critical in redefining business abilities. The concern continues to be: just how can businesses navigate this intricate terrain to really unlock the transformative power of cloud services?
Benefits of Universal Cloud Solutions
In today's hectic digital landscape, the benefits of utilizing global cloud solutions are ending up being progressively noticeable for organizations of all sizes. One main advantage is the versatility cloud services provide. linkdaddy universal cloud storage. Companies can scale their storage and computing resources up or down based on their present demands, allowing for greater agility and cost-effectiveness. Furthermore, global cloud solutions provide improved partnership abilities. Groups can quickly access, share, and work with files in real-time from throughout the globe, improving efficiency and team effort.
Safety is another critical benefit of global cloud solutions. Leading cloud company execute durable security procedures to protect data from violations, ensuring that delicate details is certified and safe with guidelines. In addition, utilizing cloud services lowers the need for extensive IT facilities on-site, conserving companies both time and cash. By outsourcing IT administration to cloud company, companies can focus on their core goals while enjoying the reliability and effectiveness that cloud solutions offer.
Secret Features to Look For
When considering global cloud solutions, businesses need to prioritize key attributes that align with their details operational requirements. Durable safety steps, such as file encryption, routine data back-ups, and conformity accreditations, assistance secure delicate details from unapproved accessibility or breaches.
Additionally, dependable efficiency and uptime are essential attributes to consider. Organizations depend on cloud solutions to be responsive and constantly available, so selecting a company with a strong track document in these locations is critical. Smooth assimilation capabilities with existing systems and applications additionally play a significant function in making the most of effectiveness and performance.
Moreover, responsive client support and solution level agreements (SLAs) that guarantee a specific degree of efficiency are indications of a quality cloud provider (universal cloud storage Service). By assessing these essential functions, services can pick a cloud solution that not just fulfills their existing needs but also supports their future growth and success
Application Finest Practices
Efficient application of cloud services rests on calculated preparation and careful implementation. To make sure an effective change to cloud-based remedies, companies must follow best techniques that maximize safety, scalability, and performance.
First of all, it is vital to examine the present IT infrastructure and define clear purposes for moving to the cloud. Comprehending the particular needs and objectives of the company will guide the option of one of the most appropriate cloud services and providers. In addition, producing a comprehensive migration strategy that describes timelines, duties, and prospective dangers is crucial for a smooth change.
Additionally, information safety and security actions ought to be a leading concern during application. Applying encryption procedures, setting up gain access to controls, and regularly keeping track of for any kind of find more security breaches are essential steps to protect delicate information in the cloud atmosphere.
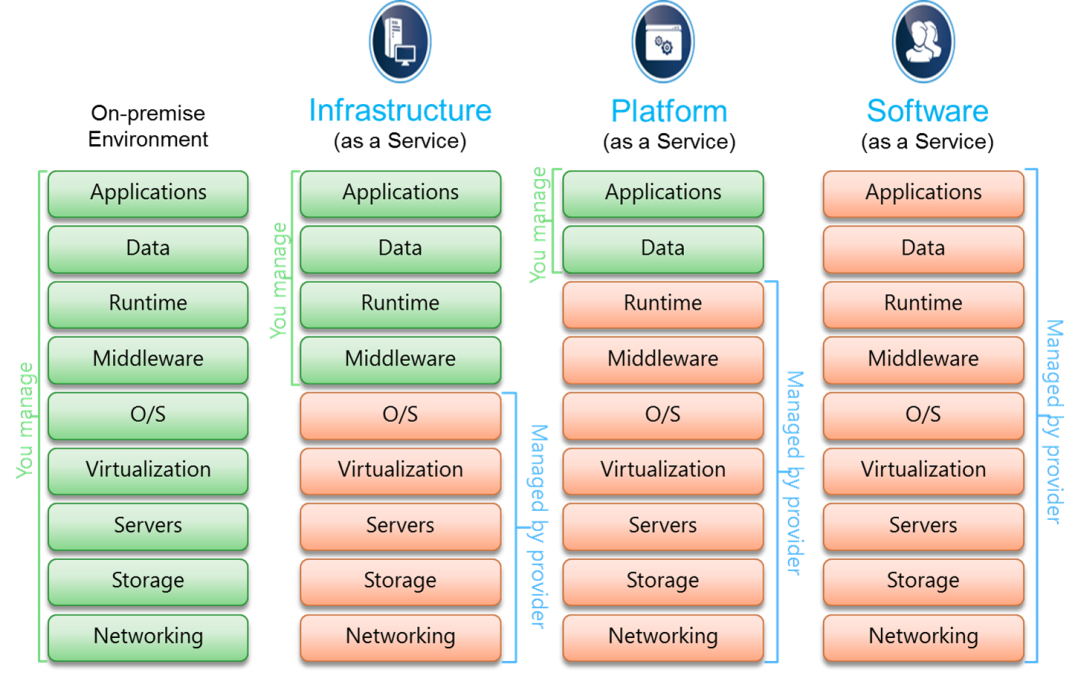
Optimizing Cost Effectiveness Approaches
To enhance and boost operational cost savings budget allowance, companies must purposefully use inexpensive methods when enhancing their usage of cloud solutions. One key approach to making best use of expense performance is to accurately examine the company's future and current needs. By understanding the particular requirements, firms can prevent over-provisioning resources, which can result in unneeded expenses. In addition, executing automated scaling devices can assist change sources based on need, making certain that the company just pays for what it uses.
Furthermore, capitalizing on discounts or booked circumstances used by cloud company can substantially lower costs. Firms need to regularly review their use patterns and readjust their plans to take advantage of any readily available cost-saving possibilities. One more efficient approach is optimizing data storage space and archiving practices to decrease unneeded prices linked with storing redundant or out-of-date information.
Protection Measures for Data Security
Executing robust security measures is essential for guarding sensitive information and guaranteeing information security in cloud solutions. With the go to these guys enhancing dependence on cloud innovation, businesses need to prioritize carrying out stringent protection procedures to minimize the dangers connected with data violations and unauthorized accessibility. Encryption plays an essential role in boosting data security by encoding details as though just licensed events can understand it. Protected verification techniques, such as multi-factor authentication and biometric confirmation, add an added layer of protection by ensuring that only confirmed customers can access sensitive data.
Normal safety and security audits and analyses are critical for identifying vulnerabilities and ensuring conformity with sector laws. Data loss avoidance devices help monitor and control data transfers, preventing unauthorized sharing of personal details. Additionally, applying security measures like firewalls, breach discovery systems, and routine security updates can strengthen the cloud facilities versus cyber hazards.
Final Thought
In verdict, the fostering of reputable global cloud services uses organizations the chance to improve performance via scalability, enhanced collaboration tools, and robust safety actions. By implementing best techniques, focusing on security, and maximizing expense performance methods, businesses can run effectively and securely in the cloud. It is important for organizations to take advantage of the versatility and benefits of global cloud solutions to remain affordable in today's electronic landscape.
Safety is another crucial advantage of global cloud solutions. Leading cloud solution companies execute robust security measures to shield information from violations, making sure that sensitive information is safe and certified with regulations. By outsourcing IT management to shadow solution companies, organizations can concentrate on their core goals while taking more info here pleasure in the dependability and efficiency that cloud solutions use.

Report this page